When trying to enable http2 in my nginx installation I ran into a problem which took me over 12 hours to solve, so I’m sharing it here in case somebody finds this helpful.
The problem was that after enabling http2 in nginx I was receiving the error ERR_SPDY_INADEQUATE_TRANSPORT_SECURITY but only in Chrome/Chromium browser! In Firefox everything was fine, and indeed firefox was using http 2.0 protocol.
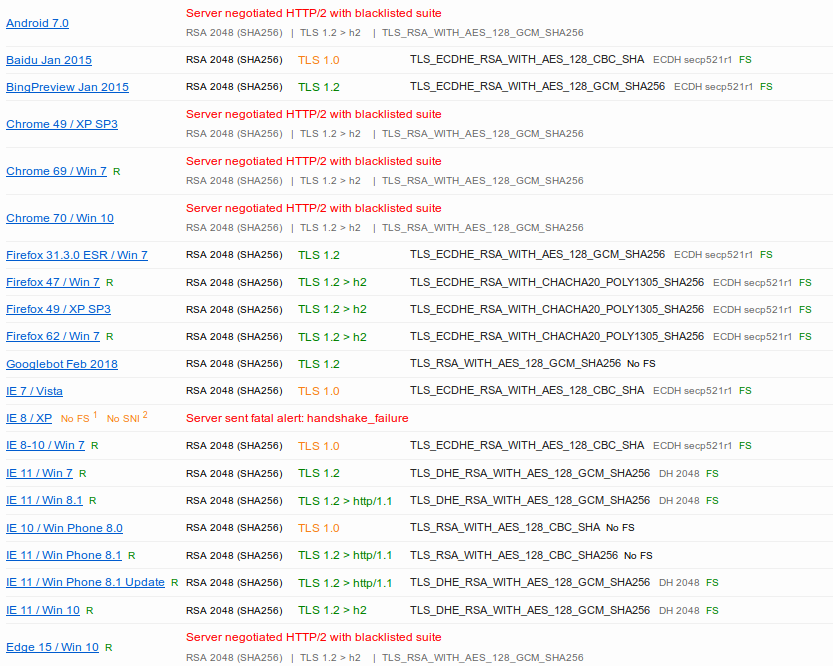
At the same time when testing my installation in https://www.ssllabs.com I was seeing several “Server negotiated HTTP/2 with blacklisted suite” errors in the following browsers:
- Chrome 49, 69, 70
- Android 7.0
- Edge 15
Initially I was thinking that the problem was in the ssl_ciphers keys, as I had read that the order plays an important role. I spent over 12 hours reordering and changing the ciphers according to www.ssllabs.com report without success…
The problem finally was not the ssl_ciphers but the fact that I was missing the following line in my nginx configuration:
ssl_ecdh_curve secp384r1;This didn’t allow some ciphers to work correctly in some browsers. For example Chrome/Chromium mistakenly was thinking my server was using the SPDY protocol, and that’s why it was reporting the ERR_SPDY_INADEQUATE_TRANSPORT_SECURITY error.
I suggest you to get a very optimized ssl_ciphers string from the following link by selecting nginx, intermediate and setting your server and OpenSSL version: https://mozilla.github.io/server-side-tls/ssl-config-generator/
This ciphers string changes often to adjust with the current safest encryption suites. At the moment of this writing this is my best selected ssl_ciphers string which gave me the widest compatibility with http2 support and an A/A+ in www.ssllabs.com.
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS'; The interesting part is that no where in internet I could find any hint for this missing line in my case. So if this post was helpful to you please drop a comment…